Configuring Threat Intelligence in Splunk Enterprise Security 
This course provides an overview of how to configure threat intelligence sources within Splunk Enterprise Security, a premium application used to support Security Operations Center operations. Learn how to maximize the value of your Splunk deployment. ▼
ADVERTISEMENT
Course Feature
![]() Cost:
Cost:
Free Trial
![]() Provider:
Provider:
Pluralsight
![]() Certificate:
Certificate:
Paid Certification
![]() Language:
Language:
English
![]() Start Date:
Start Date:
On-Demand
Course Overview
❗The content presented here is sourced directly from Pluralsight platform. For comprehensive course details, including enrollment information, simply click on the 'Go to class' link on our website.
Updated in [March 06th, 2023]
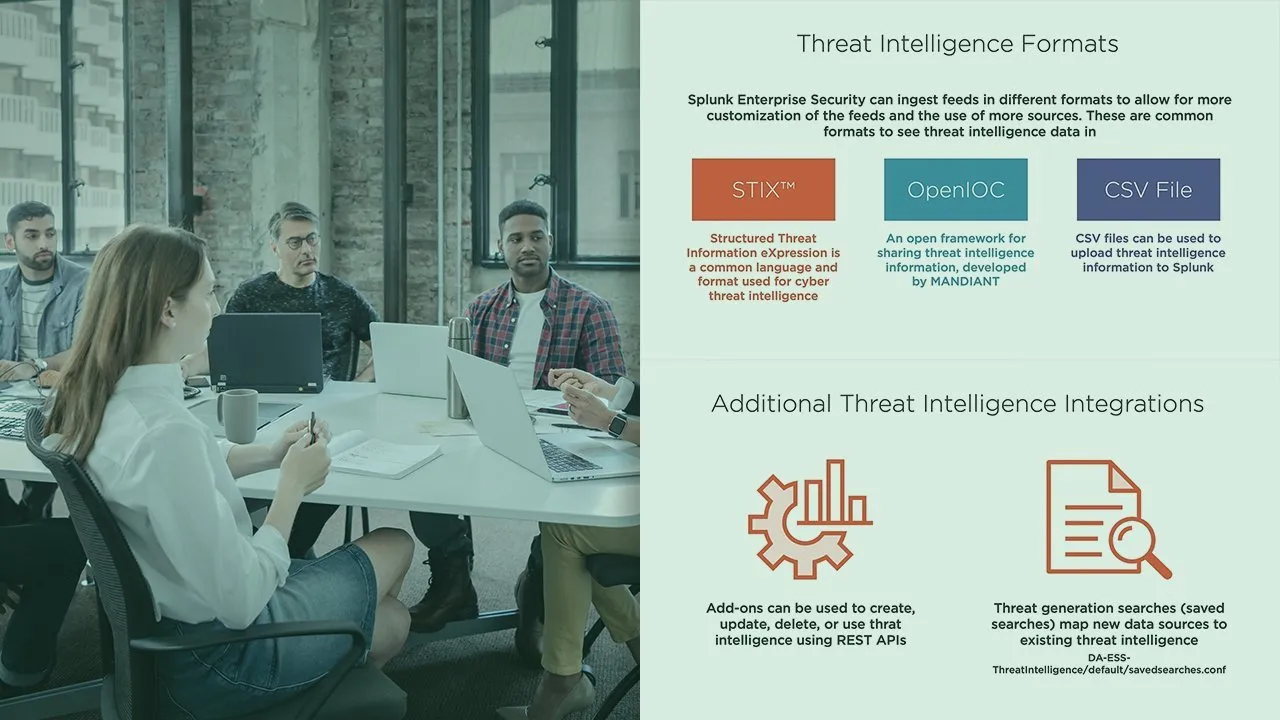
By the end of this course, you’ll have a better understanding of how to configure threat intelligence sources for use in Splunk Enterprise Security. You’ll be able to use the Splunk Threat Intelligence Framework to enrich your data and get the most out of your threat intelligence sources.
This course is designed for security professionals who are looking to get the most out of their Splunk Enterprise Security deployment. It is assumed that you have a basic understanding of Splunk and the Splunk Enterprise Security application.
In this course, Configuring Threat Intelligence in Splunk Enterprise Security, you’ll learn how to configure various threat intelligence sources for use within Splunk Enterprise Security. You’ll start by learning about threat intelligence and the different formats it comes in. You’ll then learn about the Splunk Threat Intelligence Framework and how to use it in order to enrich your data. You’ll look at the threat intelligence tools that we can use in the application as well. Finally, you’ll learn how to configure the threat intelligence sources and parse the data in order to get what you need for Splunk Enterprise Security.
By the end of this course, you’ll have a better understanding of how to configure threat intelligence sources for use in Splunk Enterprise Security. You’ll be able to use the Splunk Threat Intelligence Framework to enrich your data and get the most out of your threat intelligence sources. You’ll also be able to configure the threat intelligence sources and parse the data in order to get what you need for Splunk Enterprise Security.
[Applications]
Upon completion of this course, users should be able to apply the knowledge gained to configure various threat intelligence sources for use within Splunk Enterprise Security. They should be able to understand the different formats of threat intelligence and how to use the Splunk Threat Intelligence Framework to enrich their data. Additionally, they should be able to configure the threat intelligence sources and parse the data in order to get the information they need for Splunk Enterprise Security.
[Career Paths]
1. Security Analyst: Security Analysts are responsible for monitoring and analyzing security threats and vulnerabilities, and developing strategies to mitigate them. They must be knowledgeable in the latest security technologies and trends, and be able to identify and respond to potential threats. Security Analysts are also responsible for developing and implementing security policies and procedures. With the increasing complexity of cyber threats, Security Analysts are in high demand and the role is expected to continue to grow.
2. Security Engineer: Security Engineers are responsible for designing, developing, and implementing security solutions to protect an organization’s data and systems. They must be knowledgeable in the latest security technologies and trends, and be able to identify and respond to potential threats. Security Engineers are also responsible for developing and implementing security policies and procedures. With the increasing complexity of cyber threats, Security Engineers are in high demand and the role is expected to continue to grow.
3. Security Architect: Security Architects are responsible for designing, developing, and implementing security solutions to protect an organization’s data and systems. They must be knowledgeable in the latest security technologies and trends, and be able to identify and respond to potential threats. Security Architects are also responsible for developing and implementing security policies and procedures. With the increasing complexity of cyber threats, Security Architects are in high demand and the role is expected to continue to grow.
4. Threat Intelligence Analyst: Threat Intelligence Analysts are responsible for monitoring and analyzing security threats and vulnerabilities, and developing strategies to mitigate them. They must be knowledgeable in the latest security technologies and trends, and be able to identify and respond to potential threats. Threat Intelligence Analysts are also responsible for developing and implementing threat intelligence policies and procedures. With the increasing complexity of cyber threats, Threat Intelligence Analysts are in high demand and the role is expected to continue to grow.
[Education Paths]
1. Bachelor of Science in Cybersecurity: This degree path focuses on the technical aspects of cybersecurity, such as network security, cryptography, and computer forensics. It also covers topics such as risk management, incident response, and security policy. This degree path is becoming increasingly popular as organizations become more aware of the need for strong cybersecurity measures.
2. Master of Science in Information Security: This degree path focuses on the management aspects of cybersecurity, such as risk management, security policy, and incident response. It also covers topics such as network security, cryptography, and computer forensics. This degree path is becoming increasingly popular as organizations become more aware of the need for strong cybersecurity measures.
3. Doctor of Philosophy in Cybersecurity: This degree path focuses on the research aspects of cybersecurity, such as developing new technologies and methods for protecting networks and data. It also covers topics such as risk management, incident response, and security policy. This degree path is becoming increasingly popular as organizations become more aware of the need for strong cybersecurity measures.
4. Master of Business Administration in Cybersecurity: This degree path focuses on the business aspects of cybersecurity, such as risk management, security policy, and incident response. It also covers topics such as network security, cryptography, and computer forensics. This degree path is becoming increasingly popular as organizations become more aware of the need for strong cybersecurity measures.
Course Provider

Provider Pluralsight's Stats at AZClass
Pluralsight ranked 16th on the Best Medium Workplaces List.
Pluralsight ranked 20th on the Forbes Cloud 100 list of the top 100 private cloud companies in the world.
Pluralsight Ranked on the Best Workplaces for Women List for the second consecutive year.
AZ Class hope that this free trial Pluralsight course can help your Splunk skills no matter in career or in further education. Even if you are only slightly interested, you can take Configuring Threat Intelligence in Splunk Enterprise Security course with confidence!
Discussion and Reviews
0.0 (Based on 0 reviews)
Explore Similar Online Courses

IBM Data Warehouse Engineer

Photoshop Beginners Mastery: Zero to Hero in Photoshop

Python for Informatics: Exploring Information

Social Network Analysis

Introduction to Systematic Review and Meta-Analysis

The Analytics Edge

DCO042 - Python For Informatics

Causal Diagrams: Draw Your Assumptions Before Your Conclusions

Whole genome sequencing of bacterial genomes - tools and applications

Introduction to Splunk
Splunk: The Big Picture

Creating Workflow Actions in Splunk
 Related Categories
Related Categories
 Popular Providers
Popular Providers
Quiz
 Submitted Sucessfully
Submitted Sucessfully
1. What is the purpose of this course?
2. What type of data can be enriched using the Splunk Threat Intelligence Framework?
3. Which of the following is not a threat intelligence tool used in Splunk Enterprise Security?


Start your review of Configuring Threat Intelligence in Splunk Enterprise Security