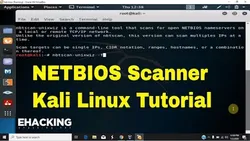
Kali Linux Hacking Tutorials 
This course provides an introduction to Kali Linux Hacking Tutorials. Learn how to hack Windows using a PDF, crack passwords, hack Android over WAN, make Kali Linux anonymous, reset root password, change user's password, hack WhatsApp, and use the QRLJacking Exploitation Framework. Gain the skills and knowledge needed to protect yourself and your data from cyber threats. ▼
ADVERTISEMENT
Course Feature
![]() Cost:
Cost:
Free
![]() Provider:
Provider:
Youtube
![]() Certificate:
Certificate:
Paid Certification
![]() Language:
Language:
English
![]() Start Date:
Start Date:
On-Demand
Course Overview
❗The content presented here is sourced directly from Youtube platform. For comprehensive course details, including enrollment information, simply click on the 'Go to class' link on our website.
Updated in [May 25th, 2023]
This Kali Linux Hacking Tutorials course provides an overview of the techniques used to hack Windows using a PDF, password cracking, and hacking tutorials. It also covers Android hacking over WAN (Remote) using Metasploit & Ngrok, making Kali Linux anonymous using TOR & Whonix, resetting the root password in Kali Linux, changing user’s password in Kali, and how to hack WhatsApp. Finally, the course covers QRLJacking Exploitation Framework.
[Applications]
After completing this course, students can apply their knowledge to a variety of tasks. They can use Kali Linux to hack Windows systems, crack passwords, and exploit Android devices over WAN. They can also use Kali Linux to make themselves anonymous using TOR and Whonix, reset root passwords, and change user passwords. Additionally, they can use QRLJacking Exploitation Framework to hack WhatsApp.
[Career Paths]
1. Cyber Security Analyst: Cyber security analysts are responsible for protecting an organization’s computer networks and systems from cyber-attacks. They use a variety of tools and techniques to identify and mitigate potential threats, such as malware, phishing, and other malicious activities. With the increasing number of cyber-attacks, the demand for cyber security analysts is expected to grow significantly in the coming years.
2. Penetration Tester: Penetration testers are responsible for testing an organization’s security systems and networks to identify any potential vulnerabilities. They use a variety of tools and techniques to identify and exploit any weaknesses in the system. With the increasing number of cyber-attacks, the demand for penetration testers is expected to grow significantly in the coming years.
3. Ethical Hacker: Ethical hackers are responsible for finding and exploiting security vulnerabilities in an organization’s systems and networks. They use a variety of tools and techniques to identify and exploit any weaknesses in the system. With the increasing number of cyber-attacks, the demand for ethical hackers is expected to grow significantly in the coming years.
4. Network Security Engineer: Network security engineers are responsible for designing, implementing, and maintaining secure networks. They use a variety of tools and techniques to identify and mitigate potential threats, such as malware, phishing, and other malicious activities. With the increasing number of cyber-attacks, the demand for network security engineers is expected to grow significantly in the coming years.
[Education Paths]
1. Bachelor of Science in Cybersecurity: This degree path focuses on the technical aspects of cybersecurity, such as network security, cryptography, and digital forensics. It also covers the legal and ethical aspects of cybersecurity, such as data privacy and security policies. This degree path is becoming increasingly popular as the demand for cybersecurity professionals grows.
2. Master of Science in Information Security: This degree path focuses on the management and leadership aspects of cybersecurity, such as risk management, incident response, and security architecture. It also covers the technical aspects of cybersecurity, such as cryptography, network security, and digital forensics. This degree path is ideal for those who want to pursue a career in the field of information security.
3. Doctor of Philosophy in Cybersecurity: This degree path focuses on the research aspects of cybersecurity, such as developing new security technologies and analyzing existing security systems. It also covers the legal and ethical aspects of cybersecurity, such as data privacy and security policies. This degree path is ideal for those who want to pursue a career in academia or research.
4. Master of Business Administration in Cybersecurity: This degree path focuses on the business aspects of cybersecurity, such as risk management, incident response, and security architecture. It also covers the technical aspects of cybersecurity, such as cryptography, network security, and digital forensics. This degree path is ideal for those who want to pursue a career in the business side of cybersecurity.
Course Provider

Provider Youtube's Stats at AZClass
Discussion and Reviews
0.0 (Based on 0 reviews)
Explore Similar Online Courses

Introduction to AutoCAD Civil 3D

Become a Portrait Pro: Family and Kids

Python for Informatics: Exploring Information

Social Network Analysis

Introduction to Systematic Review and Meta-Analysis

The Analytics Edge

DCO042 - Python For Informatics

Causal Diagrams: Draw Your Assumptions Before Your Conclusions

Whole genome sequencing of bacterial genomes - tools and applications
Learning Kali Linux

Learning Kali Linux on Windows
Learning Kali Linux
 Related Categories
Related Categories
Quiz
 Submitted Sucessfully
Submitted Sucessfully
1. What is the main purpose of Kali Linux?
2. Which of the following is a feature of Kali Linux?
3. Which of the following is a way to make Kali Linux anonymous?


Start your review of Kali Linux Hacking Tutorials